OPENAM 10.0.2 FREE DOWNLOAD
This is typical for phishing, social engineering and cross site scripting attacks. To know what we discussed during the training or to subscribe for one such program, all details are here. Browsing All Articles 66 Articles. Let me start with a word of caution. The approach a vulnerability it becomes important to use the expected access vector. This is typically via the network, local, or physically even. 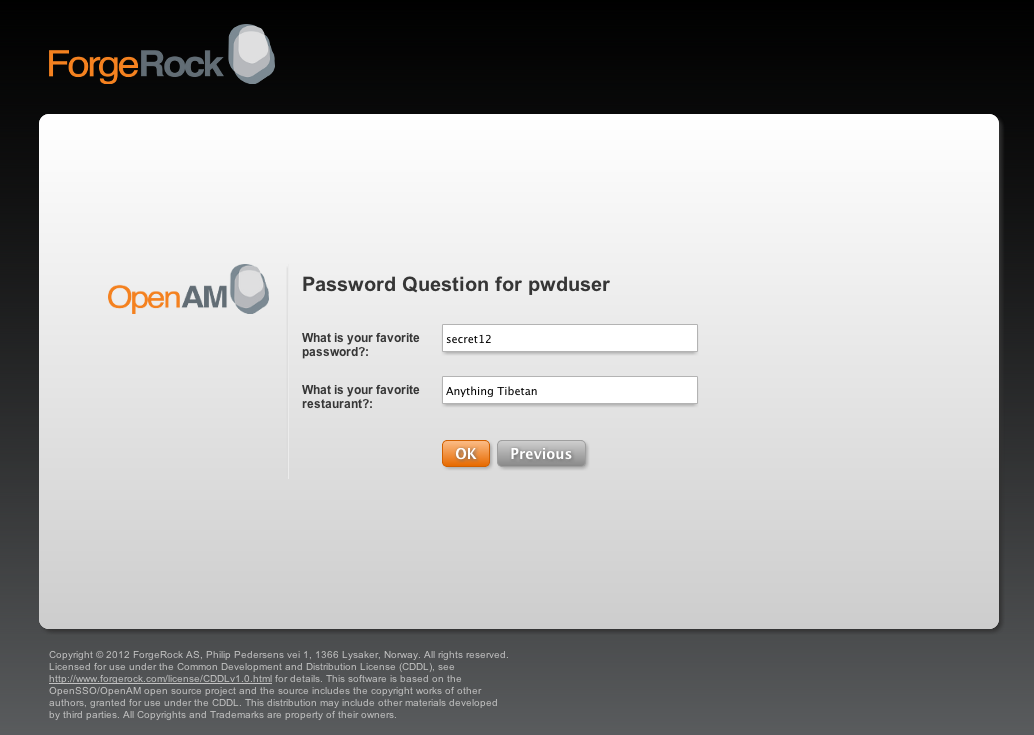
| Uploader: | Arashir |
| Date Added: | 14 December 2017 |
| File Size: | 55.99 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 43625 |
| Price: | Free* [*Free Regsitration Required] |
Finally, the SAML2 authentication module is the first module to contain the ability to perform a secondary authentication chain whose result acts as a component to this module. I really hope you get an idea on what the Distributed Authentication in OpenAM is expected to achieve. After submitting the username and password, the admin account is authenticated first and then it is also authorized to complete the impersonation request using REST calls to a specified OpenAM Policy endpoint.
Authentication Au Multiple M Single S None N The vulnerability requires an attacker to be logged into the system such as at a command line or via a desktop session or web interface. This is typically via the network, local, or physically even.
While the title suggests this might be something to enjoy with a spoon or a fork, I assure you this is not the case. Maybe you have a future project and you just want to keep in touch.
How Okta uses Okta. If all is okay, the administrator is permitted to impersonate and OpenAM creates a session for the impersonated user.
JVN# OpenAM vulnerable to denial-of-service (DoS)
Browse the Latest Snapshot. Our unique algorithm is used to identify the 0-day prices for an exploit, before it got distributed or became public. This example is only given to seed the imagination, the module currently does not restrict the impersonation session using a time window, but this is possible to do. The diagram is a slightly modified version of the one that you would have seen in my earlier blog entry.
This is also possible go via a hub to which an appliance like the home cinema would register when it is plugged in. Creating the policy set or application. Note that the API returns separate keys each time a keygen query is run. The recommendation is to deploy the relevant patches.
OpenAM – ForgeRock Community Blogs
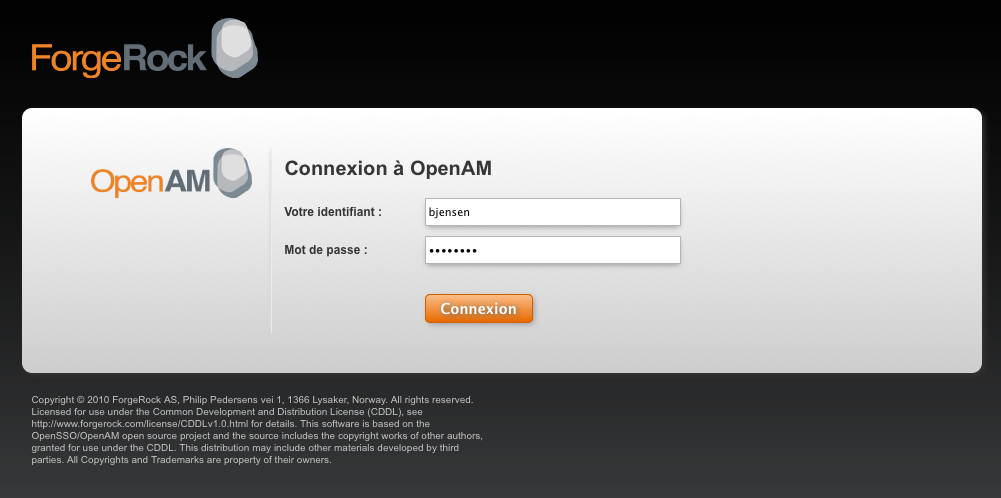
How to configure social authentication with LinkedIn. The approach a vulnerability it becomes important to use the expected access vector. OpenAM provided by ForgeRock is an open source access management software. Login to OpenAM as demo via opeenam In Google Plus, open a test account and post a phishing link. On every login attempt from a Social Login platform, the Scripted Authentication Module invokes the ZF api with an Authorization header to assess the risk associated with the login.
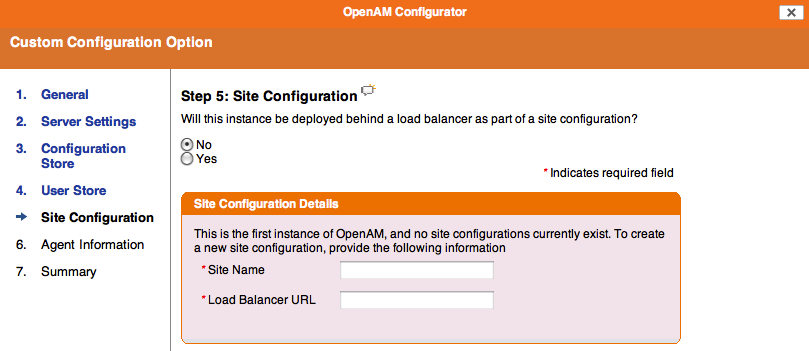
The second page of this wizard gets a bit more interesting, so here are a couple of things that you should do: Under certain circumstances this happens very fast.
To address the expanding market opportunity for identity management solutions that leverage the power of cloud, […].
Integration with PaloAlto Networks Panorama. In particular the authz-create-policy and authz-evaluate-policy-tv.
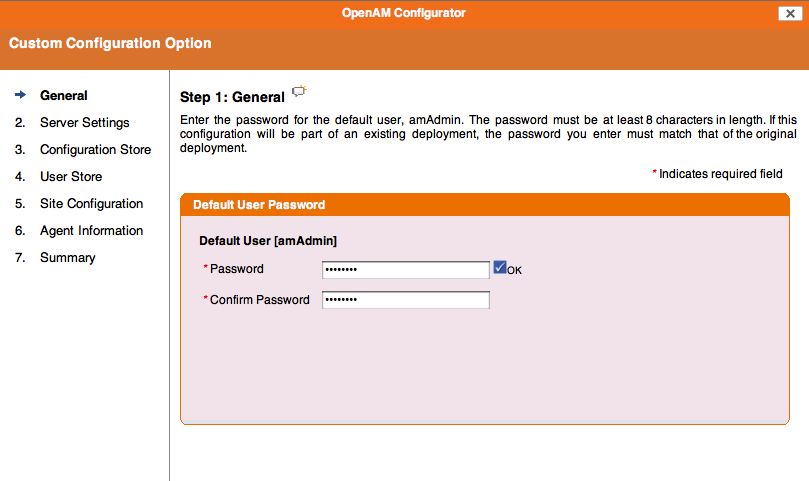
openak Chain the Scripted Authentication Module instance to the GoogleSocialAuthentication instance created in the previous step:. In case you would like to set up social authentication with other providers then that is still possible, but a bit tricky. Before getting to the video, let me mention here a couple of points:. Are you the publisher?
The token is the data record in which claims are packed, and is protected from manipulation with strong cryptography. We build an AMIdentity object for the group and validate membership.
Claim or contact us about this channel.

Comments
Post a Comment